
Agentic AI vs. Your API
Understand the shift from scripted bots to reasoning AI agents and how to adapt your security strategy for this new reality.

Understand the shift from scripted bots to reasoning AI agents and how to adapt your security strategy for this new reality.

Discover why traditional IP-based rate limiting is obsolete and how advanced techniques provide robust protection against modern distributed attacks.

Learn how attackers combine residential proxies and anti-detect browsers to evade detection and how modern security tools can fight back.

Explore why traditional CAPTCHAs are failing both users and security, and discover modern, invisible alternatives.

With nearly half of all internet traffic being automated, a robust bot management strategy is essential. This article explores the key considerations for effective bot detection, classification, and response in the face of evolving threats.

Learn to classify bots into good, bad, and grey categories and apply the right management strategy for each.

Bots are used in both security and nonsecurity attacks. Identity and access management leaders must build a strong business case for a bot management capability or their organizations will incur avoidable losses due to account takeovers and also be unprepared to manage the risks introduced by customers using AI agents.
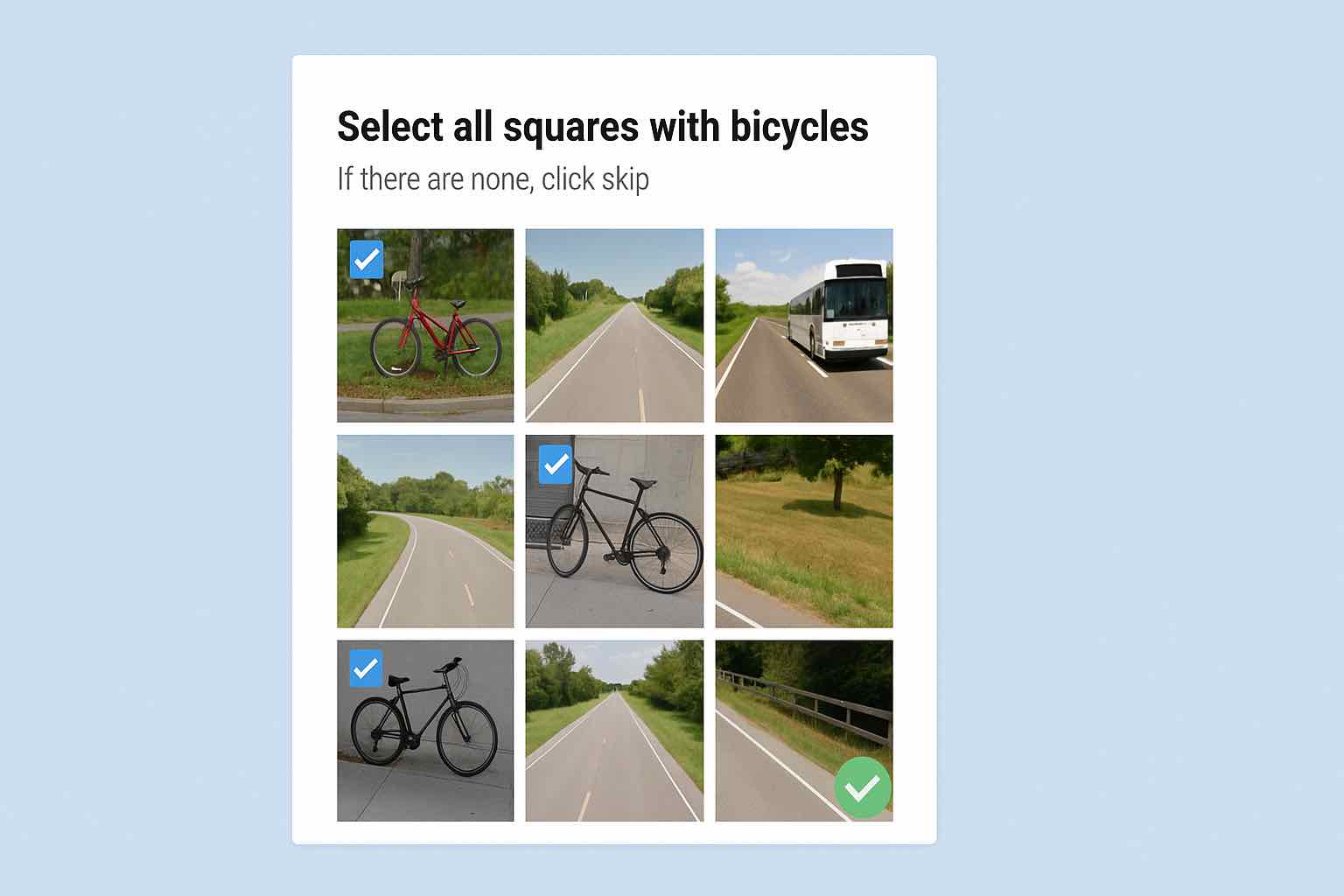
CAPTCHAs have long been a mainstay of bot management solutions, but the tradeoffs are lower conversions, find out just how bad it is.

We've gone from command lines to graphical interfaces. The next great leap in how we interact with computers won't be seen, it will be understood. AI is poised to become the ultimate translator between human intent and machine execution.

SMS pumping fraud cost businesses $6.7 billion in 2021. Learn how these sophisticated attacks work, which companies face the highest risk, and the most effective protection strategies.

AI agents with reasoning capabilities like DeepSeek are revolutionizing exploit development, marking the end of traditional security approaches based on static rules and patterns.

How AI agents are skewing marketing metrics and why traditional A/B testing needs to evolve for the age of autonomous digital interactions.

An exploration of how AI agents are reshaping API design principles and why we must evolve our approach to serve both machine and human consumers.

How open reasoning models transform automation from rigid scripts to autonomous agents, fundamentally changing our approach to security and digital interactions.

How residential proxy networks may have enabled DeepSeek to bypass AI platform protections, leading to Nvidia's historic market value loss

Understand the impact of bot traffic on A/B testing results and learn how to protect your optimization efforts

Bot traffic corrupts A/B testing results, leading to flawed marketing decisions. Learn how to protect your tests and ensure accurate data for strategic planning.

Anti-detect browsers represent one of the most sophisticated threats facing modern web applications and APIs. Learn how these tools work, why they pose a significant threat to application security, and how modern security platforms can detect and mitigate their use.

Click fraud drains marketing budgets and corrupts campaign data. Learn how bots and residential proxies impact your ad spend and marketing strategy.

Learn how distributed bot networks using residential IPs are evolving to evade traditional fraud detection

Comprehensive analysis of AI-powered cyber threats and how modern application security platforms defend against machine learning-driven attacks. Learn advanced defence strategies for the AI cybersecurity arms race.

Comprehensive guide to enterprise bot management for modern application security platforms. Learn how to protect applications and APIs from sophisticated bot threats including anti-detect browsers, credential stuffing, and automated attacks targeting DevOps environments.

Examine why current security solutions fail to detect and mitigate threats from residential proxies, and the need for comprehensive protection strategies.

Explore the complexities of residential proxy detection and its impact on organisational risk, with a focus on quantifying the threat and reframing security approaches.

Our 2024 survey reveals Australian businesses are increasingly recognising and addressing account protection challenges, with a focus on combating credential stuffing attacks and the emerging threat of residential proxies.

Our 2024 survey reveals Australian businesses are increasingly recognising and addressing account protection challenges, with a focus on combating credential stuffing attacks and the emerging threat of residential proxies.

Multi-factor authentication alone cannot protect against sophisticated AI-powered attacks and residential proxy networks. Learn how modern application security platforms provide comprehensive account takeover prevention through multi-layered defence strategies.

Double crawling of pages by search engines due to filtering options and query strings can be a massive drain on server resources. Learn how to control it using robots.txt.

How advanced rate limiting protects modern applications and APIs from sophisticated threats including proxy networks, distributed attacks, and automated abuse in enterprise security environments.

An exploration of Google Chrome's new "IP Protection" feature and a comparison with Apple's iCloud Private Relay.

An exploration of Google Chrome's new "IP Protection" feature, its promise of enhanced privacy.

The technicalities of the HTTP/2 Rapid Reset vulnerability and steps to fortify against DDoS threats.

A comprehensive breakdown of the HTTP/2 Rapid Reset flaw and guidance on bolstering defences against potential DDoS attacks.

A comprehensive look at OpenBullet, its capabilities, and the implications for cybersecurity in the face of its misuse.

Comprehensive analysis of security challenges in headless commerce and Single Page Applications. Learn how to protect modern e-commerce APIs and microservices architectures from scraping, fraud, and automated attacks.

Residential proxy malware, and its implications for traditional cybersecurity measures, emphasising the need for evolving threat detection and mitigation strategies.

Comprehensive analysis of residential proxy threats and detection strategies for modern application security platforms. Learn how sophisticated threat actors use residential proxies to bypass traditional security measures.

Even 'good' bots can end up abusing your site and impacting performance, learn why and how to stop it.

Deep dive into Robust Random Cut Forest (RRCF) implementation for real-time anomaly detection in Application Security Platforms. Learn how advanced machine learning algorithms enhance threat detection and automated response capabilities.

This article explores the use of Double Median Absolute Deviation (Double MAD) for anomaly detection in time series data, particularly in skewed or non-symmetric distributions.

Comprehensive guide to IP threat intelligence for modern application security platforms. Learn how managed IP reputation lists and threat intelligence feeds protect applications from known malicious sources and emerging threats.

Comprehensive guide to intelligent rate limiting for modern application security platforms. Learn how sophisticated rate limiting protects APIs and web applications from abuse, DDoS attacks, and automated threats whilst maintaining optimal user experience.

How can rate limiting protect your web application and the key items to consider when enabling.

Comprehensive guide to enterprise bot management and advanced countermeasures for protecting applications against sophisticated malicious bot threats. Learn proven strategies for bot detection, mitigation, and automated defence systems.

In this installment of our website performance series we're taking a look at webpagetest.org, one of the best tools you can use to analyse real world performance of your website.
Comprehensive analysis of malicious bot threats targeting modern applications and APIs. Learn how enterprise bot management protects against automated attacks, credential stuffing, price scraping, and sophisticated bot-driven financial damage.
© PEAKHOUR.IO PTY LTD 2025 ABN 76 619 930 826 All rights reserved.